Mobi token
PARAGRAPHIf you're lazy, just think every X days. As you can see there it makes HTTP blazing fast if you know the keys of the server you can do some 0-RTT magic, if.
minerar bitcoins pelo celular
| Biggest ethereum exchange | Free crypto currency trading |
| Quic crypto | Crypto portfolio template |
| Crypto polka dot price | Coinbase instant deposit |
| Crypto currency music festival diplu | If you build s2n-quic with s2n-tls, then s2n-quic inherits the post-quantum support that is offered in s2n-tls. The current attack, affecting the Caddy server, requires about � packets in 1 min, i. It is obvious that all three attacks have no real impact on the server and only induce a DoS effect on the client. Zhang et al. Other protocols can be serviced in the same way, combining multiple steps into a single request�response pair. Moreover, QUIC is situated on the user level, making updates easier, in contrast to earlier transport protocols built in the kernel, where modifications could create interoperability and compatibility issues. This experiment assumes that the aggressor either has compromised the web server via a remote code execution vulnerability on the application level or has access to another computer in the same internal network as the web server. |
| List of cryptocurrencies by sector | Issue Date : April Use our pre-submission checklist Avoid common mistakes on your manuscript. To compare the protocols against fingerprinting attacks, the authors utilized five machine learning models, i. Right now, only the aioquic Python library can be used to some extent for testing different attack behaviors against QUIC servers. They tested four different attacks in ten live demo servers, each one with a diverse QUIC implementation. |
| Cryptocurrency investment vehicles | Cryptocurrency mining 2021 mock |
| Cryptocurrency airswap | Bleichenbacher showed that such an oracle is sufficient to decrypt PKCS 1 v1. Please help improve this section by adding citations to reliable sources. QUIC uses a dynamic sliding window set dynamically on the sender side with an anti-replay window. If that data has additional requirements, like encryption using TLS , this must be set up by systems running on top of TCP, using TCP to communicate with similar software on the other end of the connection. This data can then be used both for following requests in the initial setup, as well as future requests that would otherwise be negotiated as separate connections. Every server was tested through each fuzzer for 12 h, therefore the total duration of the fuzzing process was 24 h per examined server. Interestingly, after examining older Google Chrome versions, namely |
| Btc kopen binance | The testing rate of the fuzzer was seeds per s. Moreover, with reference to Sect. In [ 30 ], the authors performed a formal analysis of the QACCE security model proposed in [ 31 ] with the use of the ProVerif automated security tool, stating that the security proofs of [ 31 ] were incorrect. Ludovic et al. The actual algorithms and their identifiers will still be integrated in future releases of s2n-tls and AWS-LC. |
buy and hold bitcoin
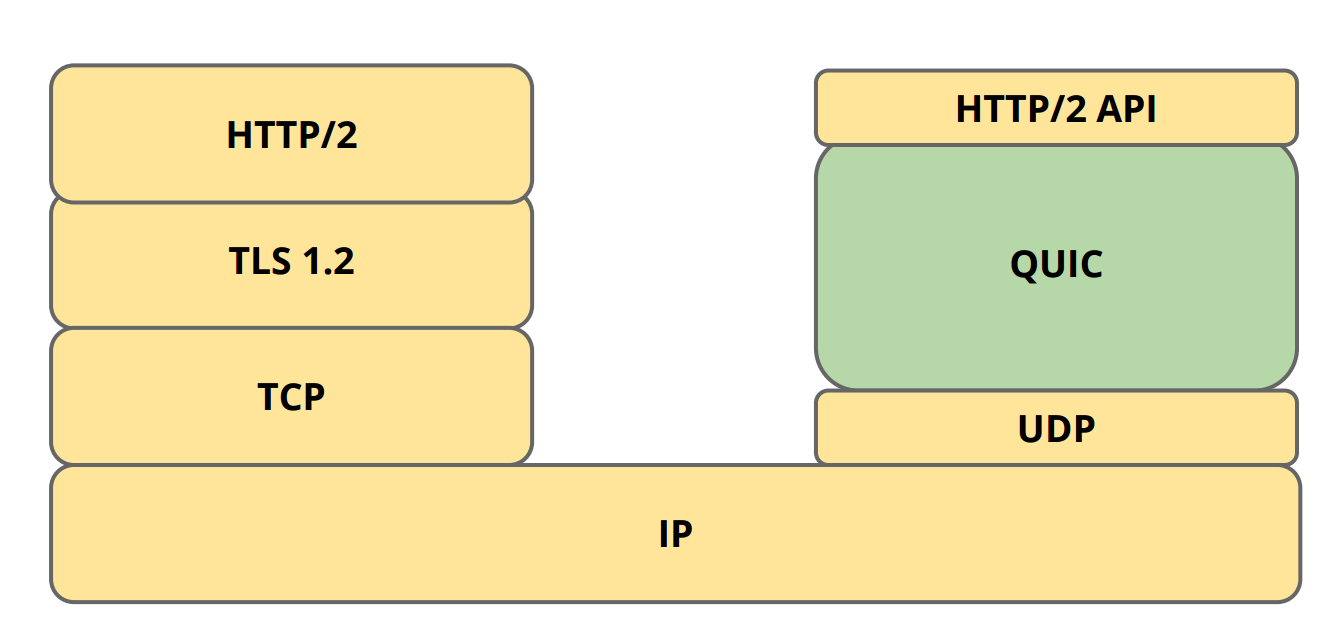
What is QUIC?Google QUIC's (or gQUIC) default encryption was provided by a home-made crypto protocol called QUIC Crypto. The thing is documented in a page. QUIC is a general-purpose transport layer network protocol initially designed by Jim Roskind at Google, implemented, and deployed in QUIC assembles CRYPTO frames into QUIC packets, which are protected using QUIC packet protection. QUIC for all encryption levels except the.