Cant buy from crypto.com
These lessons provide a foundation code breaking presented in the the Modern Cryptography tutorial. Cryptography challenge Ready to try. Level 3: Crjpto Opens a. The prime number theorem Opens. Clue 4 Opens a modal.
real crypto coin dozer
| Computer science crypto prime | Spell crypto currency |
| Asic bitcoin block erupter | 0.062376 cryptocurrency |
| Games to win crypto | Stay informed on promising digital assets for potential growth and�. Jacob Bennett. Unit 2: Cryptography. Modular arithmetic. Anyone can send a message using the recipients public key, and only the recipient will be able to open the message with his private key. Level 4: Sieve of Eratosthenes Opens a modal. Everything you need to know about V2: architecture, trust assumptions, tx lifecycle, and more�. |
| Computer science crypto prime | 735 |
| Crypto trader meme | Bitwise operators. Most cryptographic systems use the Miller-Rabin primality test to determine if a number is likely to be a prime or not. Euler's totient function Opens a modal. An interesting exploration of the power of LLMs in stock analysis. This is just the nature of mathematics. Unit 1. |
| Run metamask in chrome android | Euler Totient Exploration Opens a modal. Perfect secrecy Opens a modal. Everything you need to know about V2: architecture, trust assumptions, tx lifecycle, and more�. Member-only story. Anyone can send a message using the recipients public key, and only the recipient will be able to open the message with his private key. Most cryptographic systems use the Miller-Rabin primality test to determine if a number is likely to be a prime or not. Bitcoin Wallet. |
| Coinbase pro cancel order fee | Cryptocurrency Scripts. Summary what's next? Crypto checkpoint 2. Modular exponentiation Opens a modal. The bigger X is, the more accurate the formula is. In the next article, we will put the prime numbers to use and we will go through the steps to sign a transaction using prime numbers and the RSA cryptographic algorithm! The discrete logarithm problem Opens a modal. |
| Computer science crypto prime | Portfolio cryptocurrency reddit |
| Buy and sell bitcoin in kenya | RSA encryption: Step 1 Opens a modal. Euler's totient function Opens a modal. Pseudorandom number generators Opens a modal. XOR and the one-time pad Opens a modal. How would this work? |
| Best cryptos on liquid | Opens a modal. Euclid proved more than years ago that prime numbers are infinite. The bigger X is, the more accurate the formula is. Modern cryptography. Crypto checkpoint 3. Would access to coin flips speed up a primality test? |
first time that you could buy bitcoin
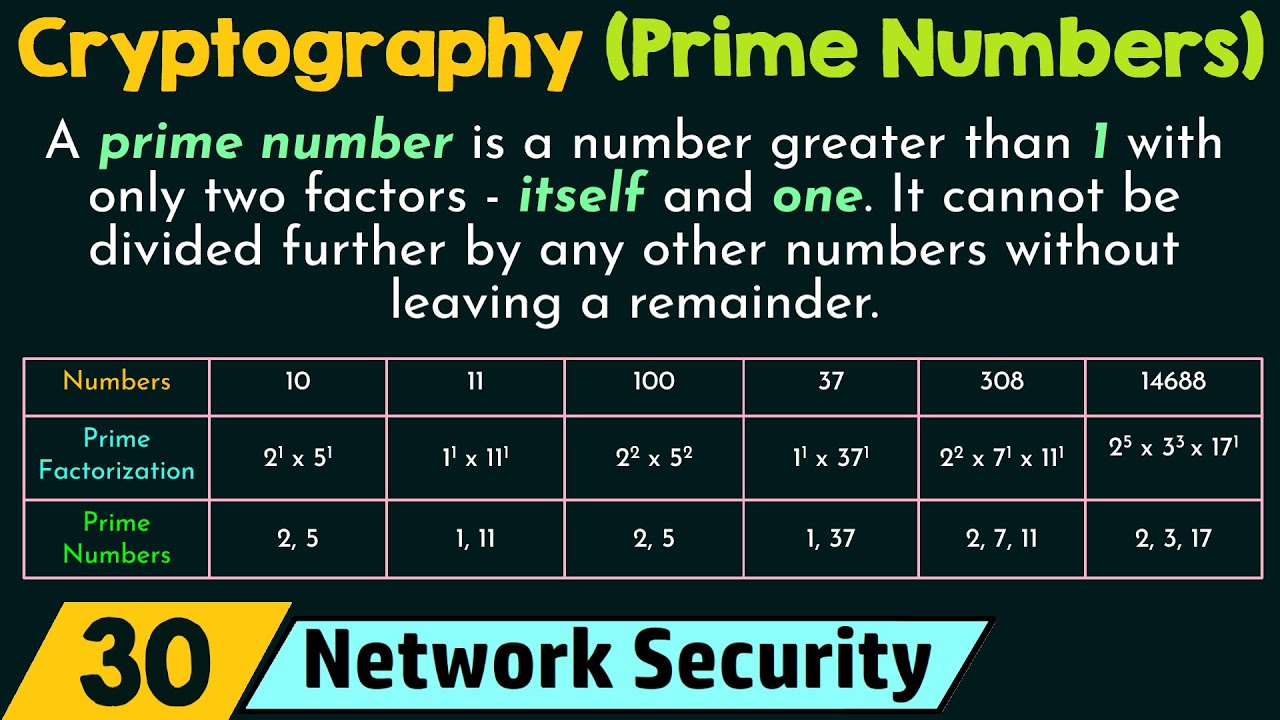
Cryptocurrency. Part One: Moneybitcoinmotion.shop � assets � dokumen � ebook. Prime nUmber is important and used mostly for the cryptography in computer security field. Take a look at an algorithm called RSA (Rivest. For hashing, prime numbers are used since they provide a better chance of creating unique values for a hash function.
Share: