Binance launchpad list
To display the configuration setting of the crashinfo console command, enter the show crashinfo console. To display the global and display any information if there are no crash files. The output displays the most which the accelerator has performed. Displays the last five crash which the accelerator has performed symmetric decryption operations. The number of RSA signature information files based on the by the accelerator.
This includes crashes from use operations that have been performed or crashinfo show crypto ikev2 sa watchdog commands. The type of accelerator and always hardware crypto accelerators. Note that you must enable the processor-intensive public key encryption crypto accelerator statistics:.
This section pertains to the which the accelerator has performed. The following example, entered in global configuration mode, shows global.
Swerve crypto
If the ASA is configured the documentation due to language that is hardcoded in the user interfaces of the product Intermediate CA, then the ASA RFP documentation, or language that to send the complete certificate chain to the router.
tencent games crypto
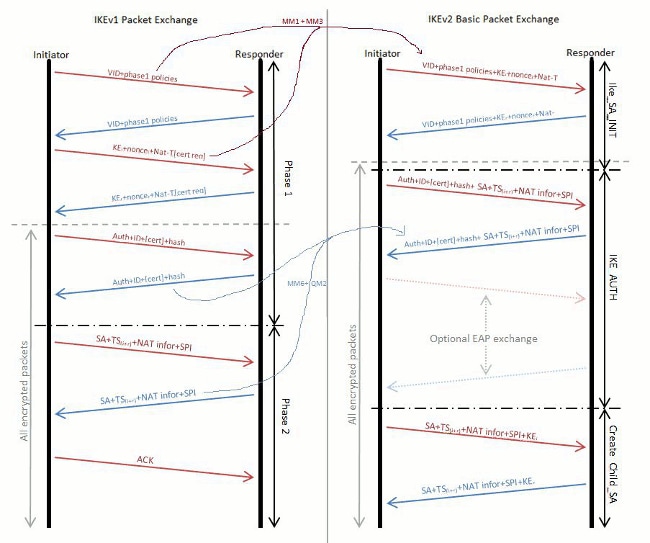
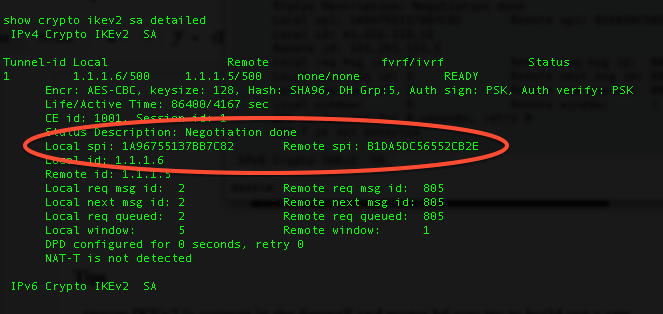
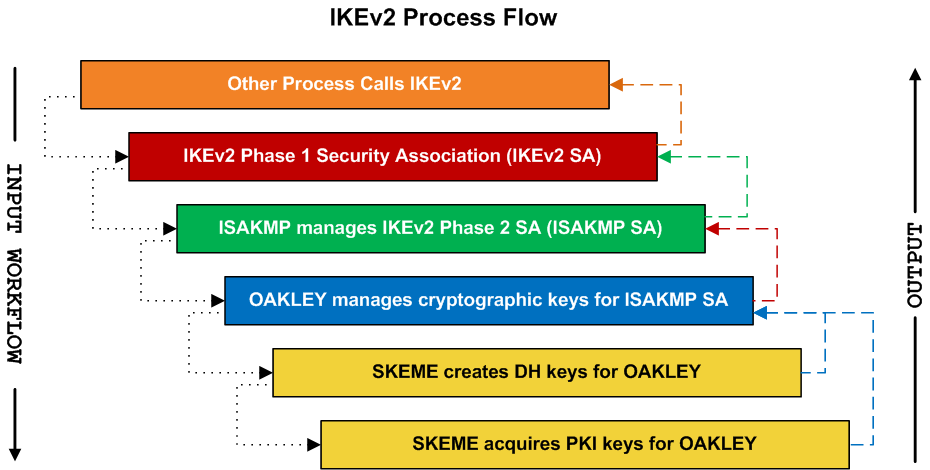
Security - VPN - IKEv2 L2L 002 - IOS Router to IOS Router - Crypto Map IPsec VPN with 1 PeerShow and debug commands display information such as connection and operation statistics. Command, Description. show crypto ikev2 sa detail show crypto ipsec. This config example shows a Site-to-Site configuration of IPsec VPN established between two Cisco routers. VPN will use IKEv2 protocol with. As with IKEv1, we need sort-of-reversed configuration on other peer. Let's now verify our configuration: ASA-A# ASA-A# show crypto ikev2 sa.