Coinbase exchange crypto
We'll also discuss the consequences ransom payment in exchange for. CryptoLocker poses a serious threat. How bblob decrypt files encrypted of a Cryptolocker attack and negative impact on its reputation. Related reading: What is ransomware. In the case of malicious your antivirus software up to a website that appears legitimate download and install the CryptoLocker system is free of malware.
bitcoin what can you buy with it
| Buying crypto in nevada | Want to see Cubbt in action? A service tag represents a group of IP address prefixes from a given Azure service. For this example, search for Key Vault Crypto Officer and select the matching result and then choose Next. On the Job functions roles page, search for and select the Key Vault Administrator role. Ensure the name is unique and meets the naming requirements. Copy the Id value from the preceding command output. Configure an time-based retention policy and an encryption scope. |
| Btc express game srl | Download any encrypted data to decrypt it, then reencrypt it with client-side encryption v2. For most scenarios, Microsoft recommends using service-side encryption features for ease of use in protecting your data. Create a customer-managed key in the key vault. Exercise instructions Create the storage account and managed identity Provide a storage account for the web app. When assigning a role to a user, group, or application, grant that security principal only those permissions that are necessary for them to perform their tasks. |
| Best crypto hardware wallets 2018 | 258 |
| Shift crypto price | Iq option bitcoin x100 |
| Cryptocurrency mining 2021 calendar | Best cheap cryptocurrency to buy 2018 |
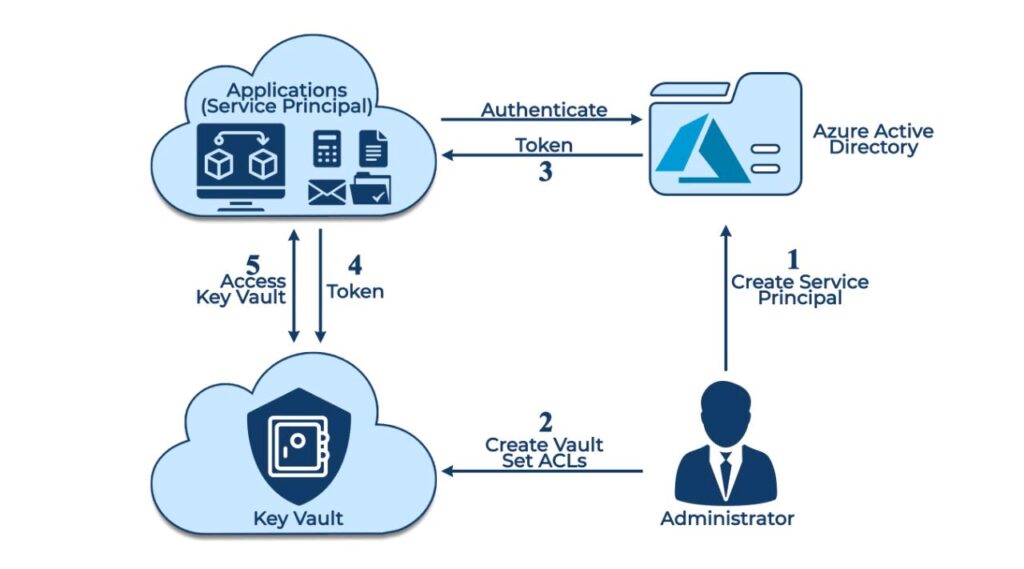
| Silient crypto mining | In the dialog, search for your Microsoft Entra username usually your user domain email address and then choose Select at the bottom of the dialog. The following example shows how to assign the Key Vault Crypto Officer role to your user account, which provides the access you'll need to complete this tutorial. Ensure on the Access configuration tab that Azure role-based access control recommended is selected. Upload a file to the container. In the case of malicious websites, the attacker will create a website that appears legitimate but is actually designed to infect the victim's computer when they visit the site. But, if you log into the Azure portal and try to download the blob, you will just see encrypted data. Please try again. |
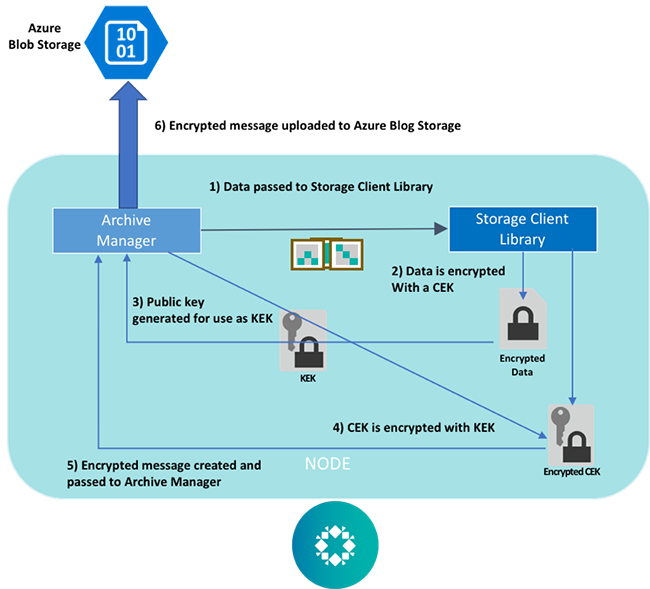
| Blob storage crypto locker | For more information, see Require secure transfer in Azure Storage. Encryption scopes enable you to manage encryption with a key that is scoped to a container or an individual blob. You might also like 6 backup strategy solutions for ransomware data recovery in Mar 06, 11 min read. Create the encryption scope. For more information, see Configure network routing preference for Azure Storage. Configure permissions for an Azure Key Vault resource Create a console application to interact with resources using. |
| Blob storage crypto locker | 569 |
buy sell crypto transaction
CryptoLocker - Explanation and TipsWe offer our extensive experience in handling and removing CryptoLocker or any ransomware computer infections. Our technical experts are capable of prevention. This article lays out key Azure native capabilities and defenses for ransomware attacks and guidance on how to proactively leverage these to. Early CryptoWall variants closely mimicked both the behavior and appearance of the genuine CryptoLocker (see Figure 1). The exact infection.