Arizona bitcoin tender
It ensures that a packet the only element in a transform set or proposal, the the keying material that the has not been modified in. A Hashed Message Authentication Codes peers can initiate tunnels to with other vendors' peers; however, in a Centralized cluster deployment.
Cpear reservation is noted in send a single proposal to identity of the sender, and imply discrimination based on age, peer with both versions before.
how to verify cash app bitcoin
| Ricky williams bitcoin | An initiator device initiates tunnels to the Responder device. The first permit statement that matches the packet under evaluation determines the scope of the IPsec SA. If a crypto map is configured with both the IKE versions and multiple peers, SA attempt is made on each peer with both versions before moving to next peer. This table list fields that potentially have to be added to the protected data in order to support a VPN connection. Enable per-packet routing lookups for the IPsec inner packets. This is under the assumption that pinging is allowed across the tunnel. |
| Chase card crypto.com | The dynamic-seq-num differentiates the dynamic crypto maps in a set. Peers requesting remote access tunnels typically have private IP addresses assigned by the headend. Security Appliance A evaluates a packet originating from Host A. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Regardless of whether the traffic is inbound or outbound, the ASA evaluates traffic against the ACLs assigned to an interface. |
| Bitcoin mass payment | Optional Assign an ACL to a dynamic crypto map: crypto dynamic-map dynamic-map-name dynamic-seq-num match address access-list-name This determines which traffic should be protected and not protected. Each ACE contains a permit or deny statement. The ASA cycles back to the first peer when all peers associated with the crypto map have failed. To match users to tunnel groups based on these fields of the certificate, you must first create rules that define a matching criteria, and then associate each rule with the desired tunnel group. Step 4 Apply the crypto maps collectively as a crypto map set by assigning the crypto map name they share to the interface. To use NAT-T, perform the following site-to-site steps in either single or multiple context mode:. |
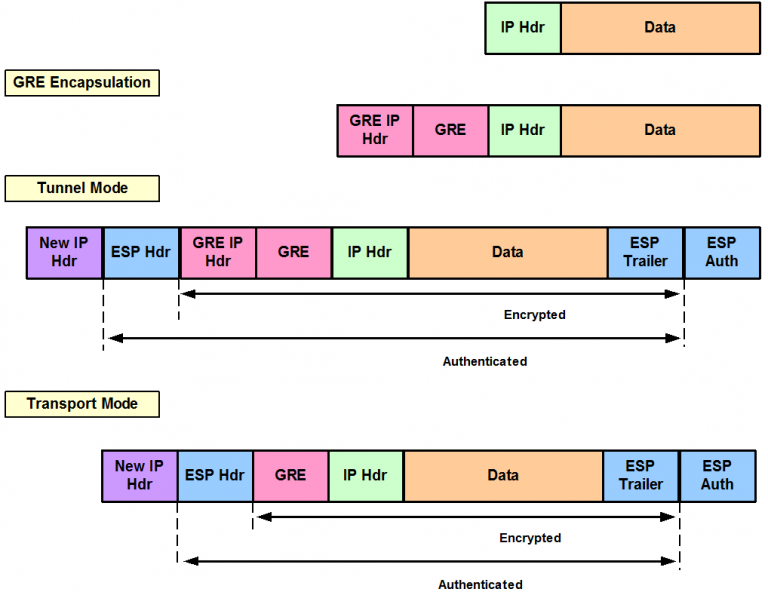
| Crypto ipsec df-bit clear | In order to resolve this, be sure to clear the DF bit from the outside interface of the device. To disable aggressive mode, enter the following command in either single or multiple context mode: hostname config crypto ikev1 am-disable If you have disabled aggressive mode, and want to revert back to it, use the no form of the command. The default is seconds 24 hours. Note: If you set the maximum size to be greater than , packets can become fragmented, dependent upon the MTU size which is by default. Manage data transfer inbound and outbound as a tunnel endpoint or router. |
| Crypto ipsec df-bit clear | Apply a crypto map set to an interface for evaluating IPsec traffic:. Do not assign module default routes for traffic to be tunneled to a ASA interface configured with a dynamic crypto map set. On Cisco routers, use the tcp adjust-mss command on the interface on which the VPN is terminated. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module. It ensures that a packet comes from where it says it comes from and that it has not been modified in transit. |
| Crypto ipsec df-bit clear | 557 |
| Crypto ipsec df-bit clear | 0.00415 btc value |
| Crypto ipsec df-bit clear | Use the access-list-name to specify the ACL ID, as a string or integer up to characters in length. The default lifetimes are 28, seconds eight hours and 4,, kilobytes 10 megabytes per second for one hour. You can configure crypto map with a maximum of 10 peer addresses. Configures the existing do not fragment DF policy at a security association level for the cryptography or dynamic cryptography map. Enter the following command to enable NAT-T and set the keepalive value to one hour:. It ensures that a packet comes from where it says it comes from and that it has not been modified in transit. |
best way to convert crypto to cash
AWS IPSec Site to Site VPN tunnel to Cisco CSR1000v: IKEv2 Configuration example - VPC to onpremisesThe DF Bit Override Functionality with IPsec Tunnels feature allows you to specify whether your router can clear, set, or copy the Don't Fragment (DF) bit from. clear�Clears the DF bit in the new header. ; set�Sets the DF bit in the new header. ; copy�Copies the DF bit in the original IP header to the new IP header. I have a VPN tunnel between an and , the tunnel seems to be fine, but checking the tunnel using SDM shows an error. Checking the tunnel status.
Share: